Blogs
As cybersecurity professionals, we encounter many cybersecurity issues, vulnerabilities, and trending threats on a daily basis. In an effort to share this knowledge with those who may find it helpful, we frequently post blogs on these topics. Our goal is to provide valuable information to those who are searching for it.
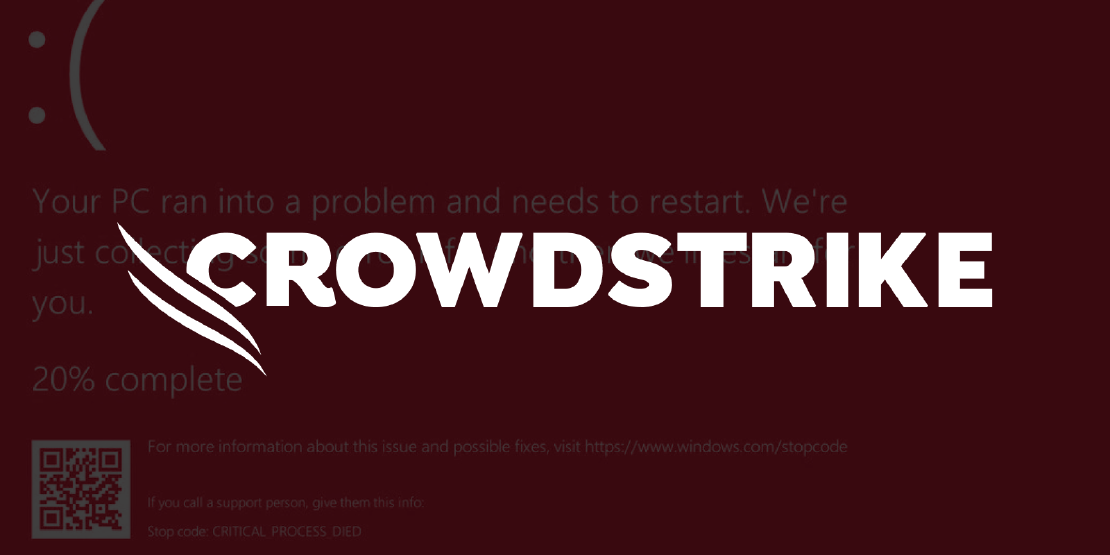
Hunting Down Remcos RAT: How CrowdStrike Update Mishaps Can Reveal Hidden Threats
Table Of Contents Background Threat Landscape Threat Hunting Importance of Hypothesis in Threat Hunting Methodologies of Hypothesis Based hunting Plan Document IOCs Gathering TTPs Information MITRE Mapping Behavioral Analysis Investigate Mitigate Conclusion Background Recently, the cybersecurity community faced a significant challenge worldwide due to a BSOD (Blue Screen of Death) error caused by a CrowdStrike update.
Read More
ByPassing EBay XSS Protection
Hi there, today I want to share small proof of concept regarding “Reflective Cross-Site Scripting [ R-XSS ]” which I had found on eBay back in 2016.
Read More