Blogs
As cybersecurity professionals, we encounter many cybersecurity issues, vulnerabilities, and trending threats on a daily basis. In an effort to share this knowledge with those who may find it helpful, we frequently post blogs on these topics. Our goal is to provide valuable information to those who are searching for it.
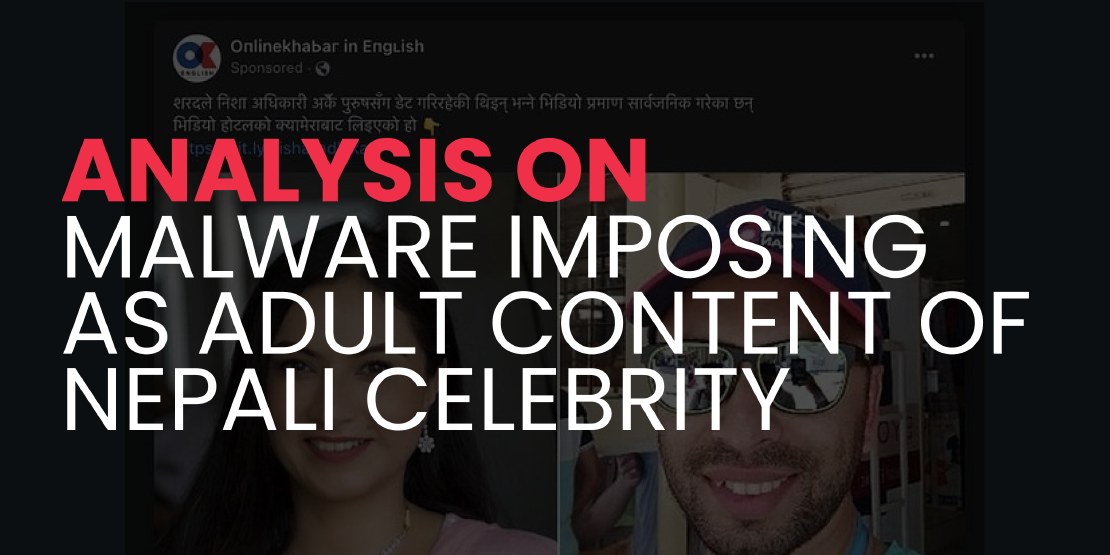
Analysis on malware imposing as adult content of Nepali celebrity
Table Of Contents Background Analysis MITRE ATT&CK TTP Further Findings Indicator of Compromise (IoC) Recommendations Background In the recent month, there is misinformation circulating concerning leaks of private video of Nepali female celebrities.
Read More
XSS on Samy Pl
In this article, I am going to explain a security issue that I found on a web site which is famous within the information security researchers.
Read More![CVE-2021-3258 | S-XSS to Defacement & Account Takeover [Q2A Themes]](/images/blog/CVE-2021-3258/7th_huefd100b93957c8ceeee9a23a5762cecf_112696_460x0_resize_q100_h2_box_3.webp)
CVE-2021-3258 | S-XSS to Defacement & Account Takeover [Q2A Themes]
In this article, I am going to share a POC (Proof of Concept) on a vulnerability that I found on a popular Forum Management System by Q2A.
Read More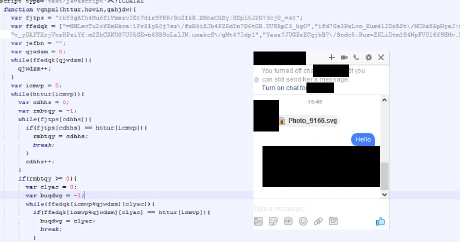
Facebook SVG Locky Ransomware Analysis
This Is What Actually Facebook’s SVG Malware Is Doing. We Had Used W3School’s IDE While Analyzing The Malicious SVG File.
Read More
ByPassing EBay XSS Protection
Hi there, today I want to share small proof of concept regarding “Reflective Cross-Site Scripting [ R-XSS ]” which I had found on eBay back in 2016.
Read More