Yojan Dhakal has been working in the Cyber Security Field for over 3 years. He specializes in Information Security Management Systems …
SWIFT CSP v2022 assessment
Table Of Contents
SWIFT CSP v2022 assessment
The Society for Worldwide Interbank Financial Telecommunications (SWIFT) is “just” a messaging system but offers its users countless services that continue to expand every year. The majority of the world’s money passes through its systems, which makes SWIFT an obvious victim of cyber-attacks. Even though its apps, services, and systems have been created with top security in mind, it’s not uncommon to hear about them SWIFT-related events in the headlines. The SWIFT program aims to detect and prevent fraudulent activity by means of a set of mandatory security controls and a community-wide information-sharing initiative.
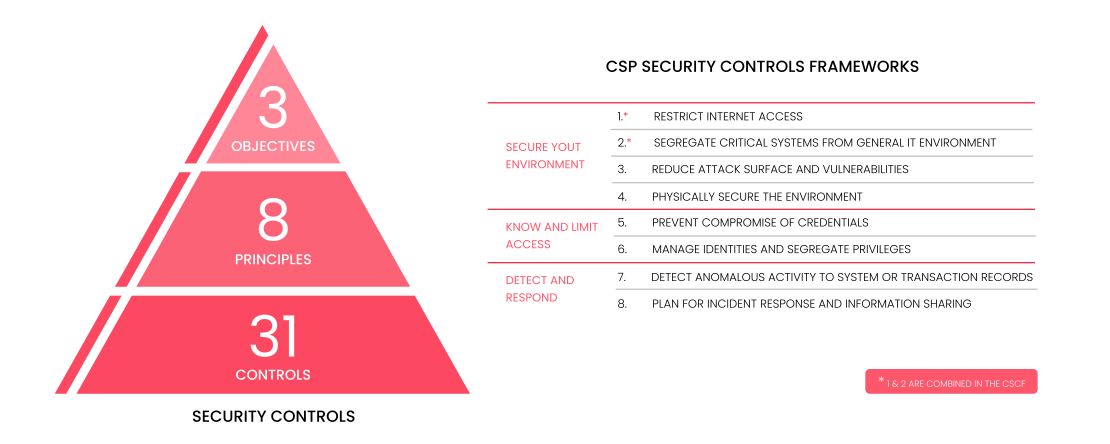
The first CSCF was introduced in 2017, has 16 mandatory and 11 advisory controls since then the scope of CSCF has improved with the introduction of new controls, definitions, and clarifications. New version v2022 of the Customer Security Control Framework (CSCF) was released in July 2021 and it includes 23 mandatory and 9 advisory security controls.
Why Is It Required?
SWIFT CSCF assists financial institutions in keeping their cyber-defenses up to date and effective to maintain the integrity of the financial network. Before yearly attesting their level of compliance, users check the security measures they have adopted with those described in the Framework. It represents a community of highly active users focused to prevent cyberattacks in their tracks, with strong attestation and compliance rates.
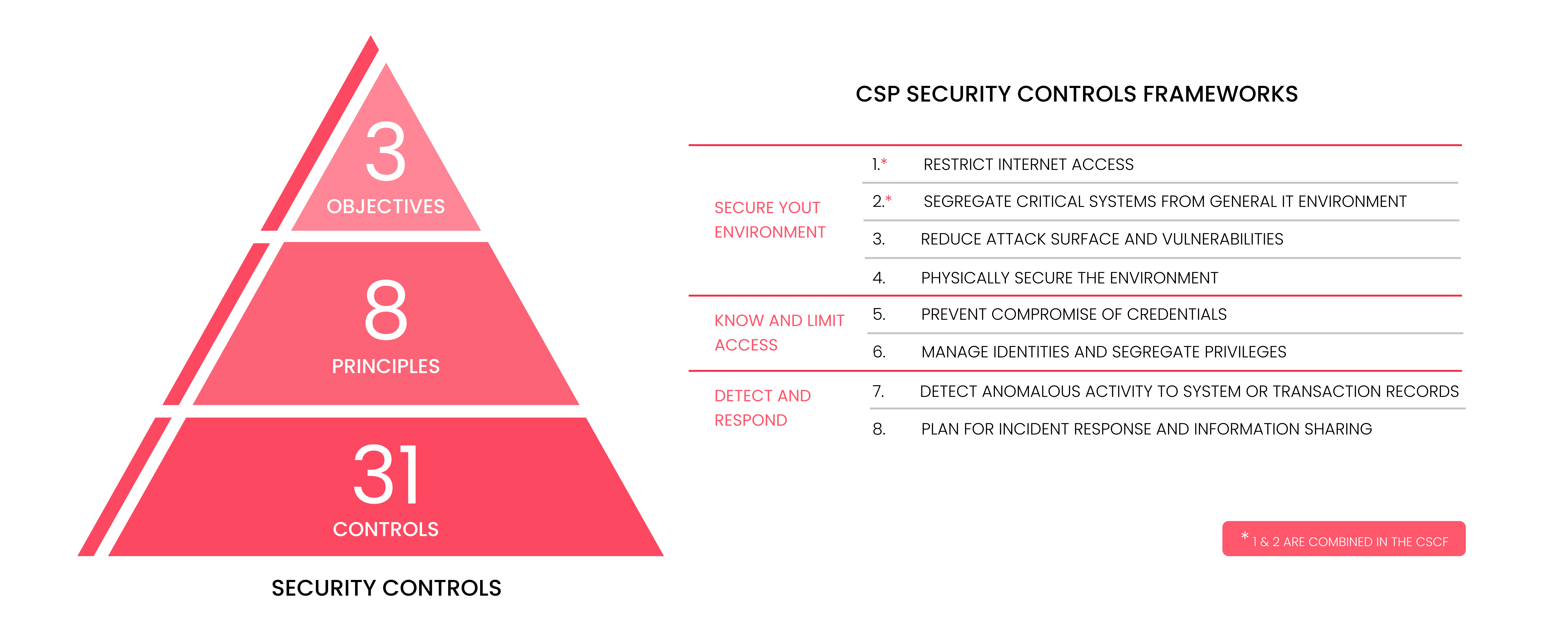
For reinforcing the security of the global banking system SWIFT CSCF has established a set of security controls divided into mandatory and advisory categories. The mandatory controls are chosen by SWIFT to set a realistic goal for near-term, tangible security gains and risk reduction. And the advisory controls are based on recommended practices that SWIFT recommends all users implement. All the security controls are articulated around three overarching objectives: Secure your Environment, Know and limit Access and Detect and Respond.
SWIFT publishes product-specific Security Guidance (SG) documents to complement the CSCF which provides the minimum-security recommendations and publishes further details of the related attestation policy and process in the policy document. The document contains:
- The requirement to attest against SWIFT’s mandatory security controls.
- The process and timelines for submitting attestation to the KYC-Security Attestation application.
- The process for viewing counterparties’ attestation via the KYC (Know Your Customer) Security Attestation application.
- Follow-up actions in case of non-compliance according to the reporting timelines.
Attestation And KYC- Security Attestation Application
Attestation acts as the evidence for the documents to prove their legitimacy of documents. Similarly in SWIFT as part of the customer security program, every SWIFT must submit an annual Security Attestation to increase community transparency. Before the expiry of the current control’s versions (31st December), all users must attest to confirming full compliance with mandatory security controls which should be followed by re-attest at least annually thereafter. The attestations must be submitted via the KYC-Security Attestation application (KYC-SA) and the latest version of the application will be released in early July every year.
The KYC Security Attestation (KYC-SA) application uses the most recent CSCF, which is accessible starting in July each year. At this time, the user can begin to assess the level of compliance against the most recent baseline.
If the user fails to submit the attestation with all mandatory security controls, SWIFT reserves the right to report to their local supervisors. And the user is in breach of the policy if:
- They do not have a valid attestation: they either did not submit an attestation, or their attestation is expired.
- They are not compliant with the mandatory controls.
- They connect through a non-compliance service provider.
- They do not complete a SWIFT-mandated external assessment.
Three Things For A Successful SWIFT Compliance
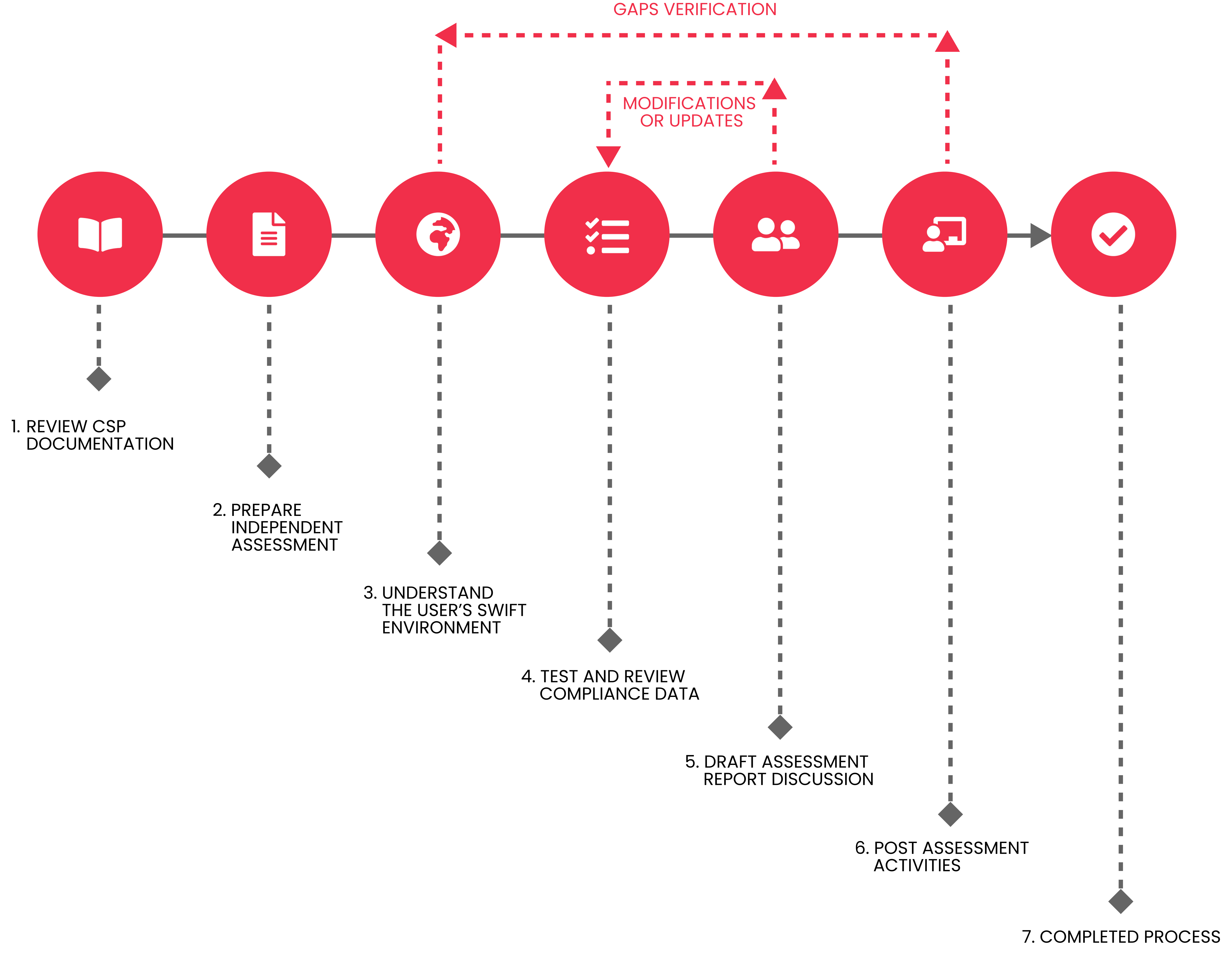
Independent assessment: Swift specifies that all attestations are independently assessed, either internally or externally. The ways for carrying out independent assessment are:
Independent internal assessment
This assessment, if performed by the second or third line of defense, is separate from the first line of defense that submitted the self-assessment. This refers to compliance, risk management, or internal audit departments that do not directly report to CISO.
Individuals performing the assessment have recent, relevant experience in assessing cyber-related security controls.
The lead assessor must hold a least one industry-relevant professional certification (e.g., CISA).
Independent external assessment
Independent auditors or CSP assessment providers, like CryptoGen Nepal, with cybersecurity assessment experience and a team of SWIFT, certified security professionals. External Assessors must be selected from the directory of CSP assessment providers.
A team comprising internal and external assessors
Assessors with industry-recognized security certifications, e.g., CISA, CISM.
The architecture of the institution: Examine and evaluate the company’s architecture to decide whether the architecture can be classified as architecture A4 or B.
Timing of the assessment: SWIFT has set a deadline of 31 December for verification and independent review. There are about two-thirds of the year left to finish the evaluation and compliance (Q3 and Q4). Institutions that make good use of this time and undertake a gap analysis will be able to benefit from moving quickly and guaranteeing compliance with the findings of their independent evaluations.
How Can CryptoGen Nepal Help?
CryptoGen Nepal provides professional-grade cybersecurity solutions for all Information Technology infrastructures. For an assessor to conduct a swift assessment, it is highly recommended that the assessing firm be listed in SWIFT’s directory of assessment providers. CryptoGen Nepal is one of the few companies from Nepal that meets the requirements for the directory listings which sets us apart from other non-listed SWIFT assessment providers. The directory is updated every two years. For listing in the Swift directory, companies must complete the updated curriculum by swift itself. The listing ensures that the company reflects the knowledge and understanding of the CSP curriculum and is eligible for conducting a SWIFT assessment.
- The attestations begin with proper planning by undertaking the available resources, CryptoGen Nepal first examines and evaluates the company’s SWIFT architecture type to recognize the applicable controls and needs to formulate a proper compliance plan to achieve and maintain CSCF v2022 compliance.
- Our independent assessment approach is based on the CSCF Independent Assessment guidelines to ensure all the necessary controls and recommendations are in place and in alignment with the operating environment.
- We provide an independent SWIFT CSP v2022 assessment report that is aligned with the practical implementations and status fulfilling requirements of SWIFT Independent Assessment Framework (IAF) and Customer Security Program (CSP) that includes Gap Assessments, Gap report along with Remediation advisory, Remediation Support, Evidence Collection, and declaration.
- We also provide assistance for the submission of the self-attestation report to SWIFT.
CryptoGen Nepal also is providing a remote or onsite Brief Presentation to explain the overall findings, measures to prevent those as recommended by SWIFT, and possible security services to enhance the security posture of the SWIFT infrastructures.