Analysis on malware imposing as adult content of Nepali celebrity
Table Of Contents
Background
In the recent month, there is misinformation circulating concerning leaks of private video of Nepali female celebrities. Following the Twitter thread from milann shrestha:
I found that the misinformation of private videos of Nepali celebrities being leaked were shared and advertised via some impersonated Facebook pages of major news sources of Nepal. This impersonation was done using puny code to make it seem similar to genuine for naked eyes.
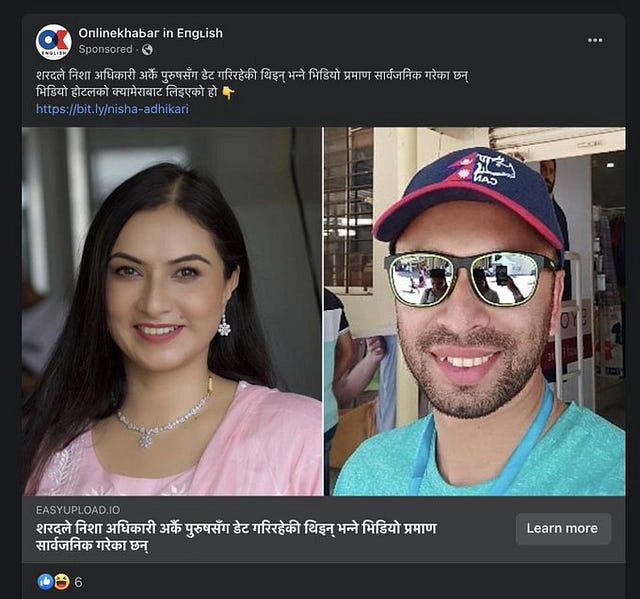
The real intent behind all this was to distribute password stealing malware. The malware samples imposing leaked private video of multiple Nepali female celebrities can be found below:
MalwareBazaar | SHA256 ae35a789f61e377dc715b0695b985d399dbcfe1650f0f10fe0ea40343fc4f0f8 (abuse.ch)
MalwareBazaar | SHA256 d2a06c261eb6864cbda29fdf43d89a167de67b1c585affa83e9852f91275ab28 (abuse.ch)
Analysis
I started my analysis with the malware sample which was imposing as private video leak of Swastima Khadka. There was a zipped file shared on drive, which on extracting included 2 files. The file icons were modified to that of a video. Additionally, the file name is lengthy with unnecessary digits possibly to hide the ‘.exe’ extension since typical users may not look at type as application. This may lead to user execution of the malware just because of video icon.
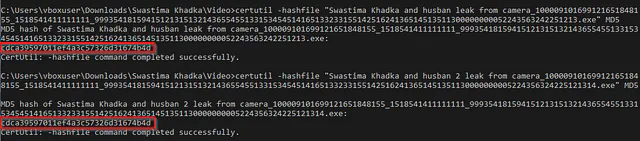
Both of the above file had exact same size. So, they could be the same file. On checking the MD5 hash of both of the file above, the hash matched and can be deduced that they were both the same file.
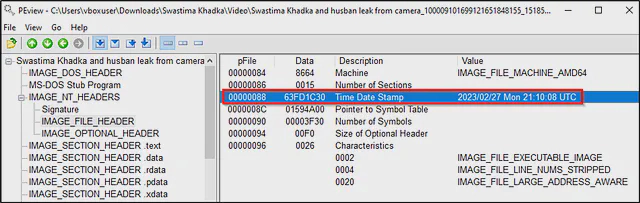
On checking the headers of the executable using PEview tool, it was found that this malware was compiled on 27th Feb of 2023.
I then fire up ProcMon tool and executed this malware in my own isolated virtual environment to understand the behavior of the malware. Here, I found that the malware was making network connection to 167[.]179[.]66[.]121:1337.
![167[.]179[.]66[.]121:1337 & vultrusercontent[.]com](/images/blog/analysis-on-malware-imposing-as-adult-content-of-nepali-celebrity/5_hu8f52946ab26fa9b75e0490165bae1397_43520_640x213_fit_q100_h2_box.webp)
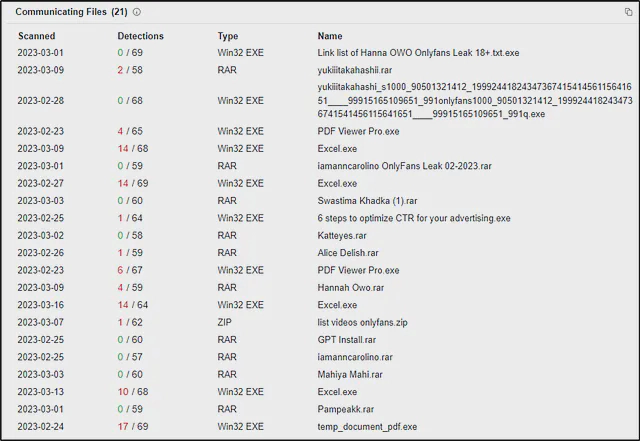
Furthermore, on checking the IP address 167[.]179[.]66[.]121 over VirusTotal, I found that this IP is associated to other possible malicious file that were also imposing as adult content and others. So, it is clear that this threat actor tries to lure its victim by imposing adult contents.
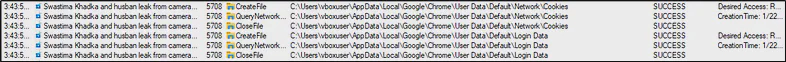
Now back to ProcMon tool, it was also found that the malware accessed the data stored by the browser. The malware accessed the default user’s cookies and login data of the Chrome browser from %LOCALAPPDATA%\Google\Chrome\User Data.
Wireshark was used to capture all the network traffic of the malware during the execution. I looked up for the above IP address 167[.]179[.]66[.]121 found in ProcMon. There it can be seen that the malware was communicating with that IP address over port 1337.
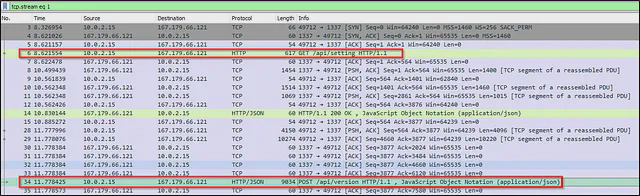
First the malware can be seen contacting the C2 server (hxxp://167[.]179[.]66[.]121[:]1337/api/setting) with GET method to get configuration. Then the malware exfiltrated the browser data containing cookie and password, along with the IP data through POST method in JSON as shown below.
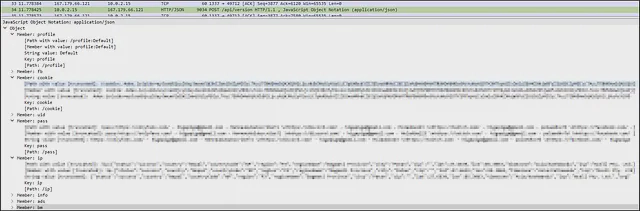
This verifies that it is a password stealer malware targeting the browsers.
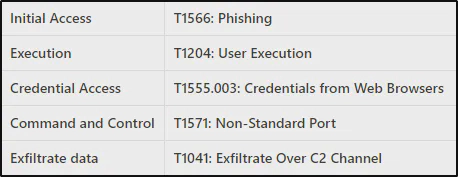
MITRE ATT&CK TTP
Further Findings
The second malware sample which was imposing as private video leak of Nisha Adhikari, also used the similar TTP as covered above. But, the only difference was the IP address of its C2 server, which was 149[.]28[.]150[.]40.
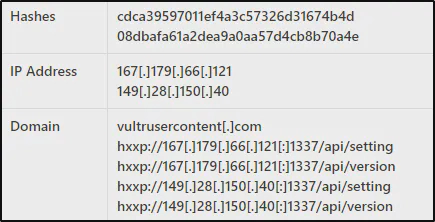
Indicator of Compromise (IoC)
Recommendations
- Do not download files from untrusted source.
- Use updated antivirus.
- Update all the password stored in the infected machine and implement multiple factor authentication.
- Destroy all web session cookies.