Analysis on Stock Trading Nepal malware campaign
Table Of Contents
Background
In the recent event of time, there has been increase in scam and malware incidents in Nepal. As a security analyst with prime interest in malware, I carried out my research. During my investigation, I came across a Facebook page, named Stock Trading Nepal. This page appeared to be offering information and resources related to stock trading. But was distributing malware and scamming people. This page was recently created on Dec 9, 2022, and is still active.
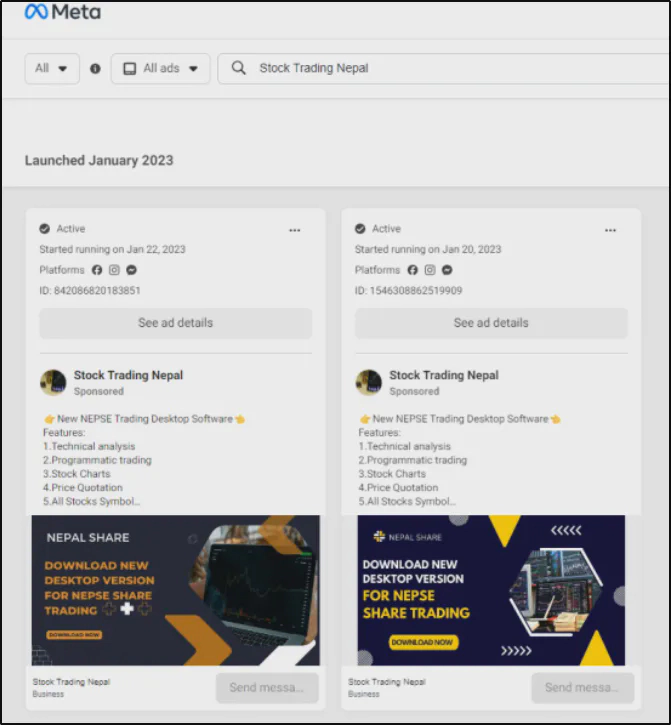
The Stock Trading Nepal page was running advertisements. I thus looked through Meta Ads Library and discovered two of their sponsored posts, where they were promoting their new NEPSE Trading Desktop program. They had two of their advertisement posts running from Jan 20 and Jan 23 of 2023. Through the advertisement, they had managed to deliver to their targeted audience.

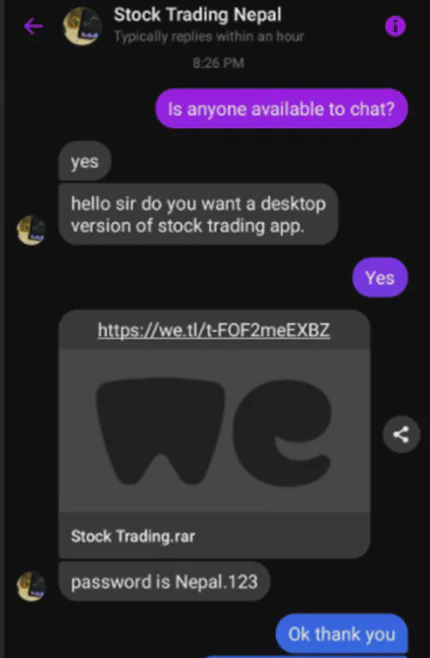
I wanted to get a hold of their file so that I could analyze it. I messaged them and immediately got their responds, where they offered their stock trading app. The file was a password protected rar file named ‘Stock Trading.rar’ and shared through WeTransfer, a temporary file sharing platform.
Still after getting hold of their application, I strike further communication so that I could obtain more information from them. After a while they started replying in Nepali, so it’s confirmed that Nepali are involved in this. Later, I told them that I had executed their application and asked for help, to which they replied with an offer to share their guide and then just ignored the messages. It’s because they just wanted that application to be executed, since the harm will be done after the execution, which analysis will be covered below.
Analysis
I downloaded the application shared by Stock Trading Nepal in my lab. On extracting the provided rar file, there was a ‘Stock Trading.exe’ executable. I started by uploading the file to the VirusTotal to scan it with different antivirus engine. This application was flagged as malicious by several security vendors. Out of 69, 32 of security vendors flagged it as malicious.
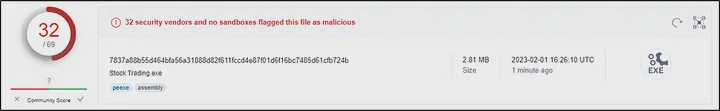
Link to VirusTotal scan: https://www.virustotal.com/gui/file/7837a88b55d464bfa56a31888d82f611fccd4e87f01d6f16bc7485d61cfb724b/detection
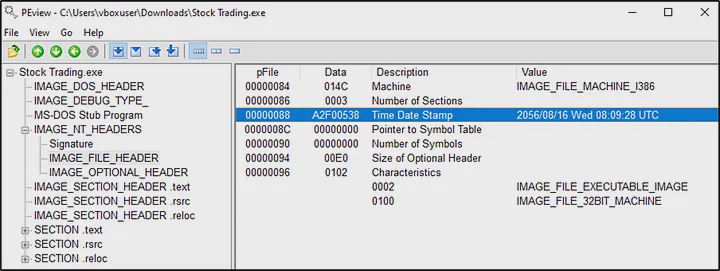
Then I checked the file header of that application, the time date stamp of the file, which showed the creation date to be 2056/08/16 08:09:28 UTC. This is impossible and is evident that time stomping is carried out on this executable.
The executable was then uploaded in an online sandbox environment, AnyRun to get an overview of the executable. On checking network connection, it was found that the executable connected to 172[.]173[.]180[.]63 over the port 80 which was flagged malicious. And on checking process, it was found that it first executed a PowerShell child process to run some base64 encoded command and then another ‘Stock Trading.exe’ child process, which was flagged as redline. Redline is a malware that harvest credential information from browser, system and crypto wallets. The fact that this malware can be purchased from underground forums makes it readily available for everyone.
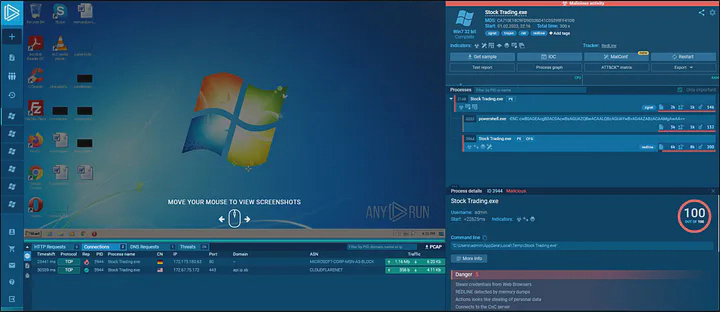
Link to AnyRun scan: https://app.any.run/tasks/e331ae77-f68e-40d9-9d0a-0432928eaab9
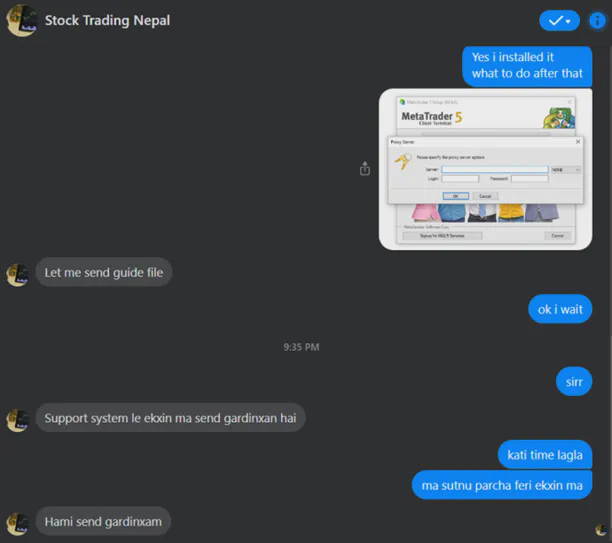
With the overview from the online sandbox results, I then focus on analysis of the executable in my own lab. On execution of the ‘Stock Trading.exe’, a GUI window popped for MetaTrader 5 client terminal setup. To the normal users, it looked like setting up a legitimate stock trading application named MetaTrader 5. But there is lot more going on the background.
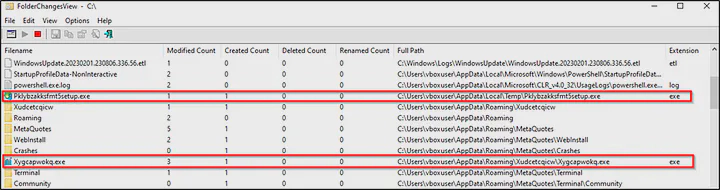
On checking the file that had been dropped by this executable using FolderChangesView tool, it was found that two executables were dropped; ‘Pklybzakksfmt5setup.exe’ under the Temp folder and ‘Xudcetcqicw.exe’ under Roaming folder of AppData.
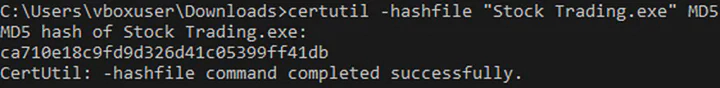
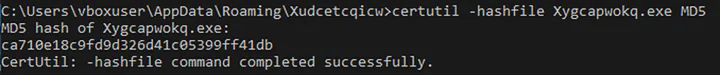
Here, the ‘Pklybzakksfmt5setup.exe’ is the MetaTrader 5 setup executable. And, ‘Xudcetcqicw.exe’ was the same ‘Stock Trading.exe’ executable as verified by the MD5 hash.
On checking the processes using Procmon tool, the results were similar to that from AnyRun. The ‘Stock Trading.exe’ first had a PowerShell child process with base64 encoded command, which make the executable sleep for 20 seconds. After that, another two child processes ‘Pklybzakksfmt5setup.exe’ and ‘Stock Trading.exe’ were executed, where the ‘Pklybzakksfmt5setup.exe’ is the MetaTrader 5 setup executable and ‘Stock Trading.exe’ is the possible Redline malware.
To analyze further on the ‘Stock Trading.exe’ child process, ‘hollows_hunter’ tool was used to dump out this process.
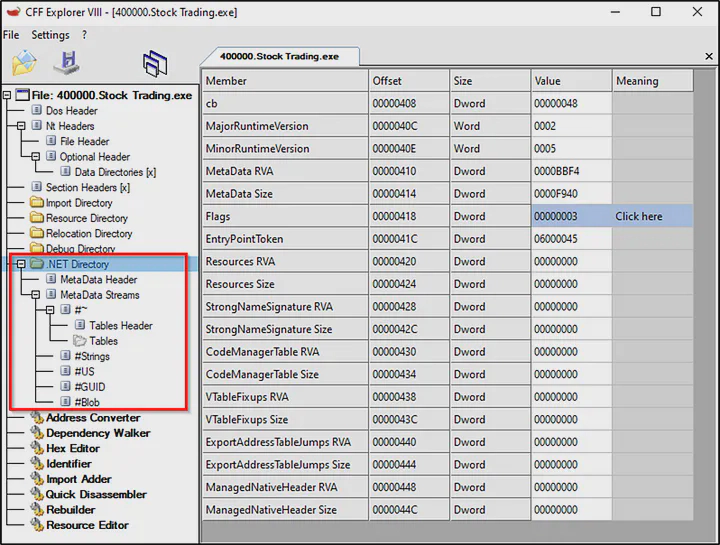
On checking it on CFF explorer, I found a .NET directory in it. So this program was written in .NET.
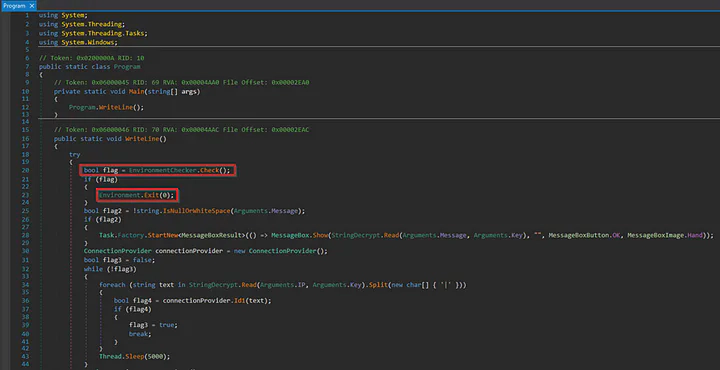
I then opened up the dumped ‘Stock Trading.exe’ in dnSpy to decompile the .NET program. After decompiling, I jumped to the entry point of this malware. I found that after its execution, the malware first checks the country where the malware is being executed. If the country falls under the list of its RegionsCountry then it will terminate itself with Environment.Exit(0).
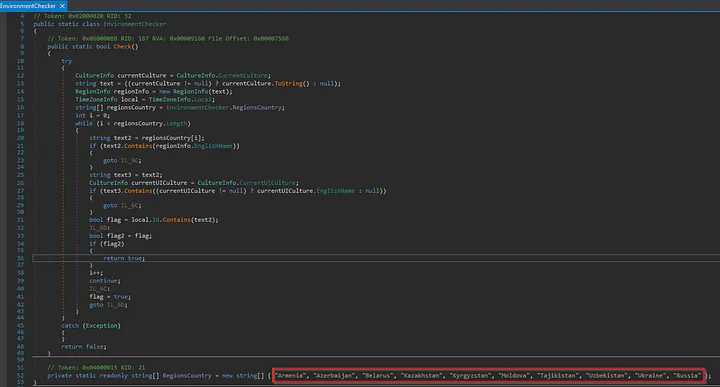
Afterward, the malware check its arguments; consisting of IP, ID, message, key and version. But the IP and ID arguments are obfuscated.
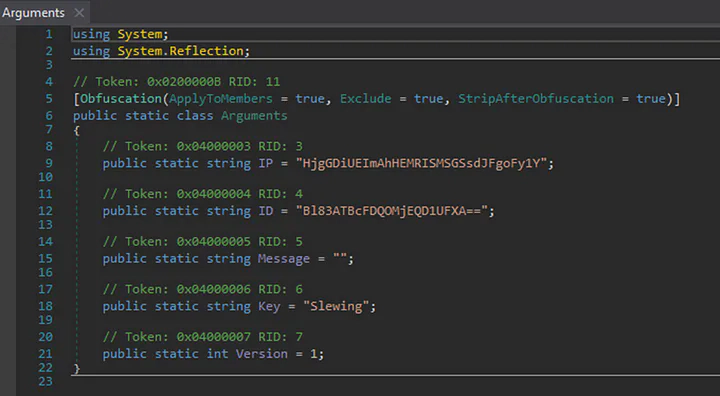
There was a StringDecrypt class, which contained the process for decryption. The obfuscated argument needs to be first decoded from base64. Then, should be XOR using the key argument from above, i.e., Slewing. And, then should be subjected to base64 again to get the final decrypted text.
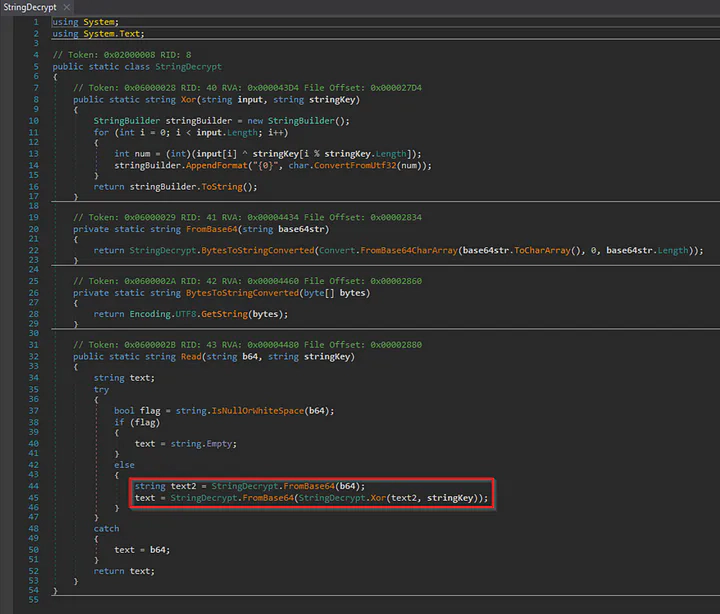
I used the above concept and decoded the IP and ID arguments using CyberChef. The IP and ID arguments were found to be 172[.]173[.]180[.]63:80 and ‘Stock market’ respectively.
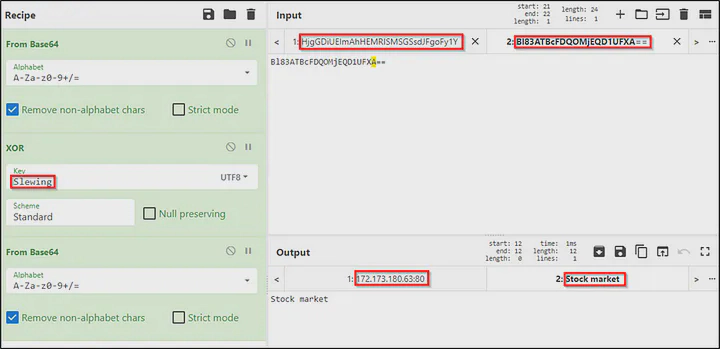
I had run Wireshark when executing this malware to capture its network traffic. I looked up for the above IP address and found the malware to be communicating with it over port 80.
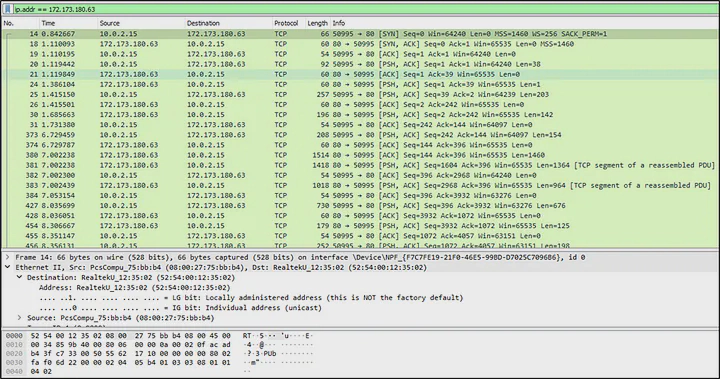
On following the TCP stream, it was found that this malware was downloading configuration from its C2 server at 172[.]173[.]180[.]63 over port 80.
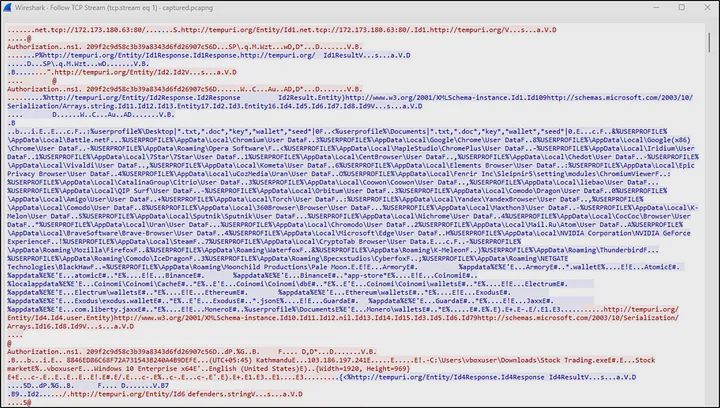
The configuration includes the following paths targeting different applications:
- %userprofile%\Desktop
- %userprofile%\Documents
- %USERPROFILE%\AppData\Local\Battle.net
- %USERPROFILE%\AppData\Local\Chromium\User Data
- %USERPROFILE%\AppData\Local\Google\Chrome\User Data
- %USERPROFILE%\AppData\Local\Google(x86)\Chrome\User Data
- %USERPROFILE%\AppData\Roaming\Opera Software
- %USERPROFILE%\AppData\Local\MapleStudio\ChromePlus\User Data
- %USERPROFILE%\AppData\Local\Iridium\User Data
- %USERPROFILE%\AppData\Local\7Star\7Star\User Data
- %USERPROFILE%\AppData\Local\CentBrowser\User Data
- %USERPROFILE%\AppData\Local\Chedot\User Data
- %USERPROFILE%\AppData\Local\Vivaldi\User Data
- %USERPROFILE%\AppData\Local\Kometa\User Data
- %USERPROFILE%\AppData\Local\Elements Browser\User Data
- %USERPROFILE%\AppData\Local\Epic Privacy Browser\User Data
- %USERPROFILE%\AppData\Local\uCozMedia\Uran\User Data
- %USERPROFILE%\AppData\Local\Fenrir Inc\Sleipnir5\setting\modules\ChromiumViewer
- %USERPROFILE%\AppData\Local\CatalinaGroup\Citrio\User Data
- %USERPROFILE%\AppData\Local\Coowon\Coowon\User Data
- %USERPROFILE%\AppData\Local\liebao\User Data
- %USERPROFILE%\AppData\Local\QIP Surf\User Data
- %USERPROFILE%\AppData\Local\Orbitum\User Data
- %USERPROFILE%\AppData\Local\Comodo\Dragon\User Data
- %USERPROFILE%\AppData\Local\Amigo\User\User Data
- %USERPROFILE%\AppData\Local\Torch\User Data
- %USERPROFILE%\AppData\Local\Yandex\YandexBrowser\User Data
- %USERPROFILE%\AppData\Local\Comodo\User Data
- %USERPROFILE%\AppData\Local\360Browser\Browser\User Data
- %USERPROFILE%\AppData\Local\Maxthon3\User Data
- %USERPROFILE%\AppData\Local\K-Melon\User Data
- %USERPROFILE%\AppData\Local\Sputnik\Sputnik\User Data
- %USERPROFILE%\AppData\Local\Nichrome\User Data
- %USERPROFILE%\AppData\Local\CocCoc\Browser\User Data
- %USERPROFILE%\AppData\Local\Uran\User Data
- %USERPROFILE%\AppData\Local\Chromodo\User Data
- %USERPROFILE%\AppData\Local\Mail.Ru\Atom\User Data
- %USERPROFILE%\AppData\Local\BraveSoftware\Brave-Browser\User Data
- %USERPROFILE%\AppData\Local\Microsoft\Edge\User Data
- %USERPROFILE%\AppData\Local\NVIDIA Corporation\NVIDIA GeForce Experience
- %USERPROFILE%\AppData\Local\Steam
- %USERPROFILE%\AppData\Local\CryptoTab Browser\User Data
- %USERPROFILE%\AppData\Roaming\Mozilla\Firefox
- %USERPROFILE%\AppData\Roaming\Waterfox
- %USERPROFILE%\AppData\Roaming\K-Meleon
- %USERPROFILE%\AppData\Roaming\Thunderbird
- %USERPROFILE%\AppData\Roaming\Comodo\IceDragon
- %USERPROFILE%\AppData\Roaming\8pecxstudios\Cyberfox
- %USERPROFILE%\AppData\Roaming\NETGATE Technologies\BlackHaw
- %USERPROFILE%\AppData\Roaming\Moonchild Productions\Pale
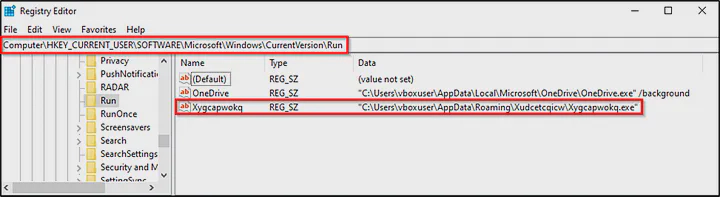
Furthermore, the malware had tried to be persistence by adding the previously dropped file ‘Xudcetcqicw.exe’ to the registry at HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run to install itself for autorun at Windows startup.
Detection Through SayCure
SayCure is custom-built monitoring, detection and response system developed by Cryptogen Nepal. It provides continuous monitoring, unified visibility, threat detection and and compliance for any environment.
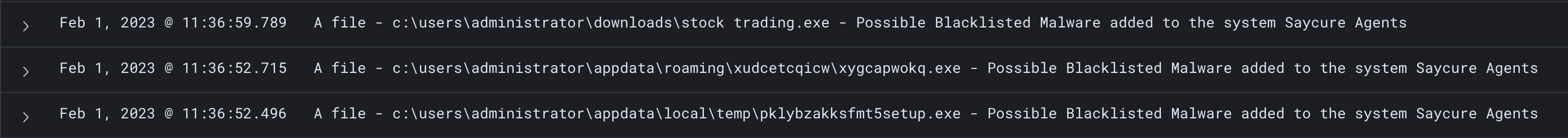
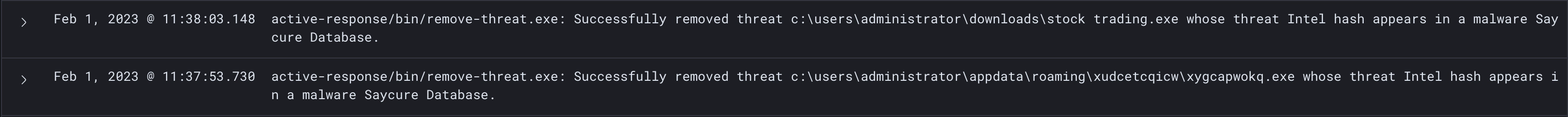
The ‘Stock Trading.exe’ malware was executed in one of the agents of SayCure. SayCure was not only able to detect the ‘Stock Trading.exe’ as potential malware, but also the two files that were dropped by the malware, i.e. ‘Pklybzakksfmt5setup.exe’ and ‘Xudcetcqicw.exe’, were also detected, as shown below.
The dashboard offered by the SayCure is a powerful tool that provides a comprehensive view of all the security-related events and incidents occurring in the network, increasing visibility to identify potential threats and respond to them quickly.
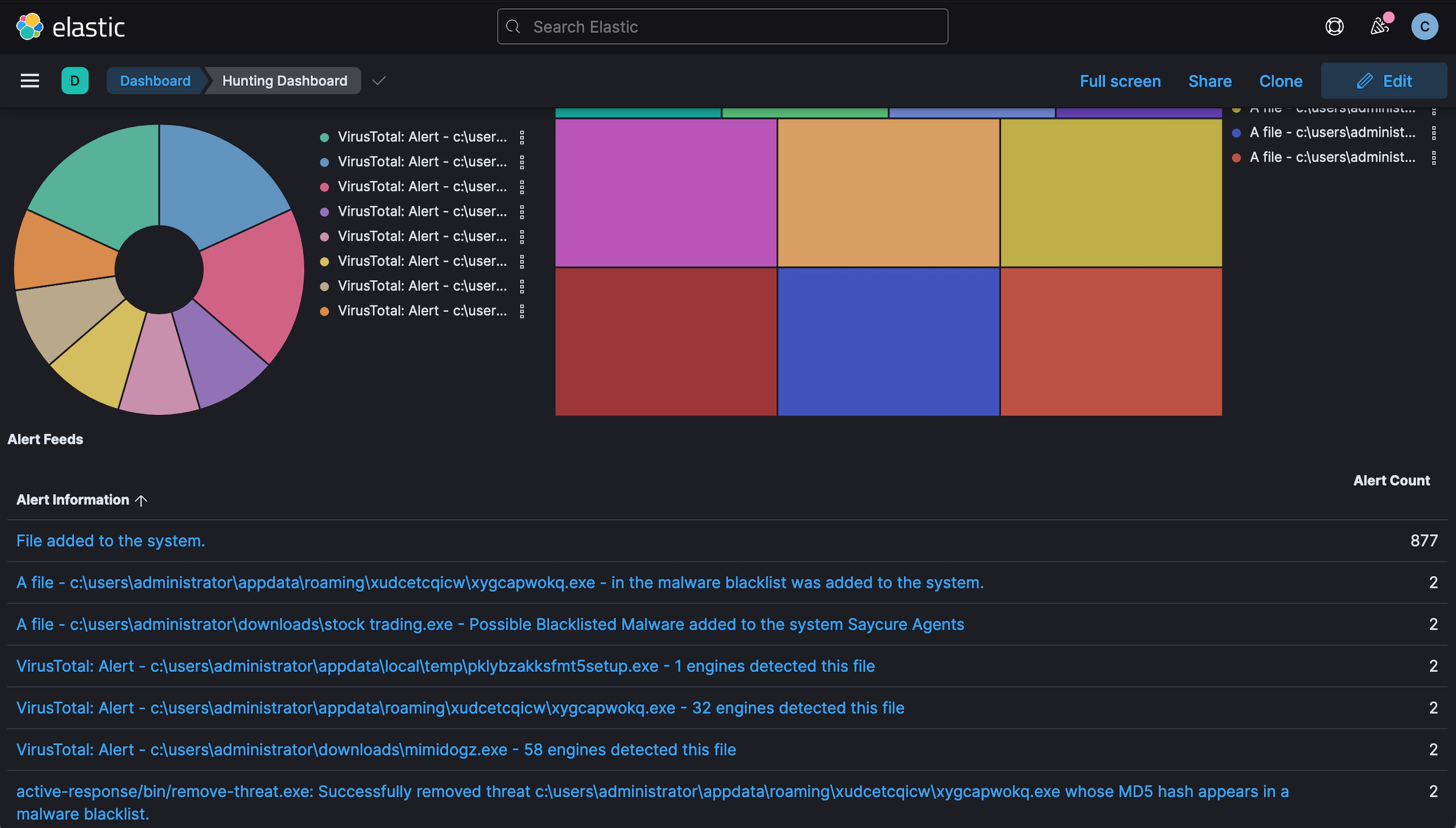
SayCure can detect and neutralize threats before they have negative impact. As shown below, SayCure was also able to quickly remove those malware after detection through its active response feature.
Indicator of Compromise
- C2 - 172[.]173[.]180[.]63
- ‘Stock Trading.exe’ - ca710e18c9fd9d326d41c05399ff41db
- ‘Pklybzakksfmt5setup.exe’ - 07906a40a9aa773564e58d5b1e86bb9a
Further Findings
I messaged the Stock Trading Nepal with other different accounts. They provide their application through WeTransfer and shared password protected file named ‘Stock Trading.rar’. But, the hash of the extracted ‘Stock Trading,exe’ was different. So they modified their malware to change it’s hash to bypass security depending on checking hash. But I found following behavior of the malware to be common across different samples:
- The malware will have timestomping to tamper the creation date.
- The malware on execution will look like MetaTrader 5 setup.
- The malware will drop ‘Pklybzakksfmt5setup.exe’ under Temp, which is MetaTrader 5 setup.
- The malware will also drop [SomeFileName].exe under Roaming, which it will add in registry at HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run for persistence.
- The malware will contact to its C2 server at 172[.]173[.]180[.]63 over port 80 to get its further configuration then steal data as per the configuration.
Recommendations
- Do not download files from untrusted source.
- Use updated antivirus.
- Update all the password stored in the infected machine and implement multiple factor authentication.
- Destroy all web session cookies.