Nirmal Dahal boasts an extensive tenure in the cybersecurity industry, where he has consistently fortified numerous enterprises against …

MEGA's Unlimited Cloud Storage Vulnerability
Background
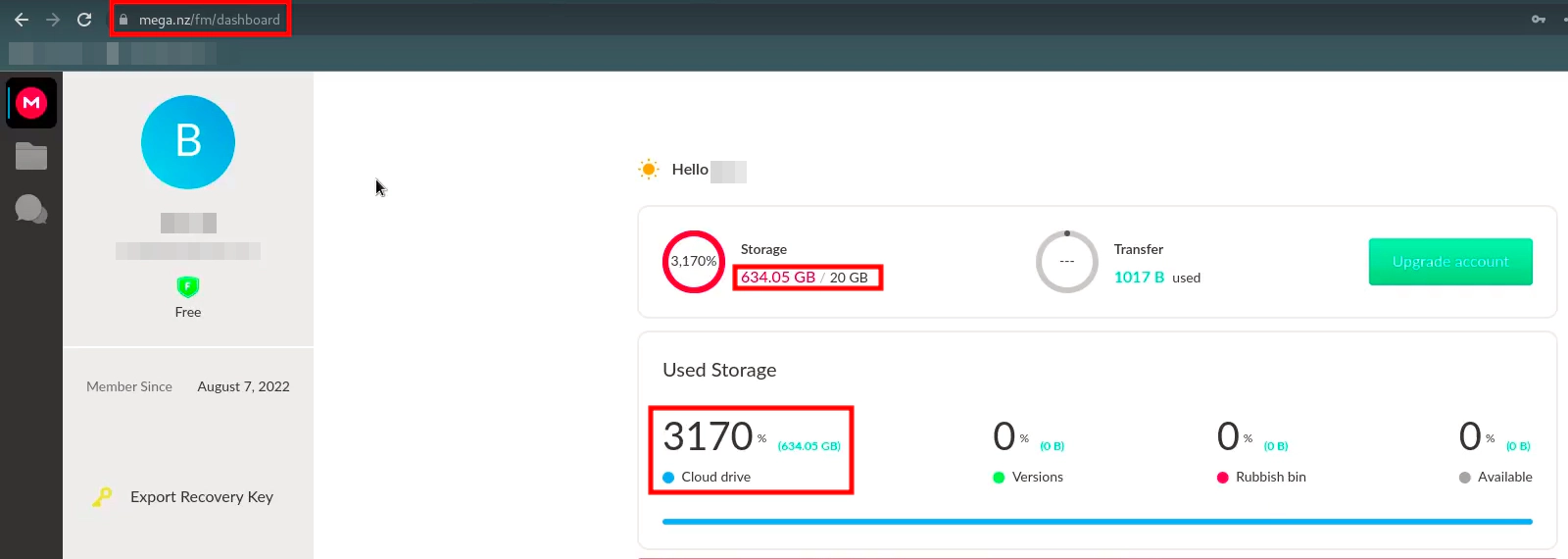
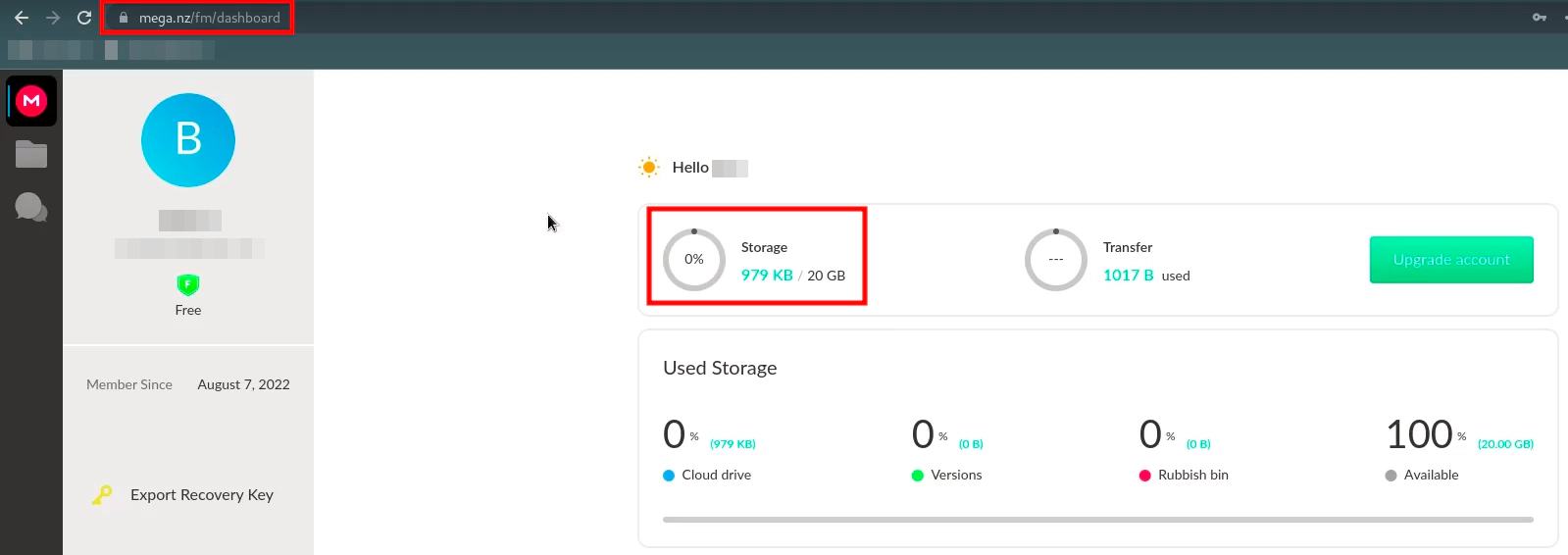
Back in June 2022, I found a flaw in the MEGA cloud storage system that let me store more data than they permit for free accounts. I was able to store roughly 1300GB data in MEGA, despite the fact that the free account storage restriction for MEGA is 20GB.
I did not use any tools to exploit the vulnerability, nor did I purposefully look for the vulnerability; if you are a regular reader of my blogs, you may be aware that I am not an active bugbounty hunter. I discovered this vulnerability while storing data, Surprisingly.
However, I reported the vulnerability almost one month after discovering it, and this is likely why I received a duplicate.
Issue
MEGA users can use the “IMPORT” feature to copy other people’s MEGA files or folders onto their own MEGA account using link. If you have a MEGA account, you can import data to your account within the limit of your subscription plan. For example, let’s say you subscribed to the MEGA “Pro Lite” plan and have 400GB storage. Now assume you get MEGA link of 500GB of Hacking Materials like PDF, Videos, and Tools somehow but your account storage limit is 400GB.
Technically, MEGA shouldn’t allow you to store the data because it is 100GB more than the plan you have subscribed to, and MEGA wasn’t letting you to do so using the Web Version, but I tried the same using the MEGA App which was installed in my Android mobile and BINGO, it allowed me to store more than my plan (despite the fact that it is a free account with a 20GB storage limit) and to verify, I tried to IMPORT other links with data and combined I was able to store approximately 1300GB of data, which is 6500% of my free plan of 20GB.
Impact
Since the MEGA’s source of revenue is from the sell of the Storage Services they offer to customers, if anyone can use the Storage more than they are limited to, they will not buy the storage, resulting in a financial loss to MEGA.
Steps of Reproduction
Create an account using the MEGA Web or Mobile Portal.
Verify the newly created account using the link in your email from MEGA.
Your free storage limit is displayed on the homepage.
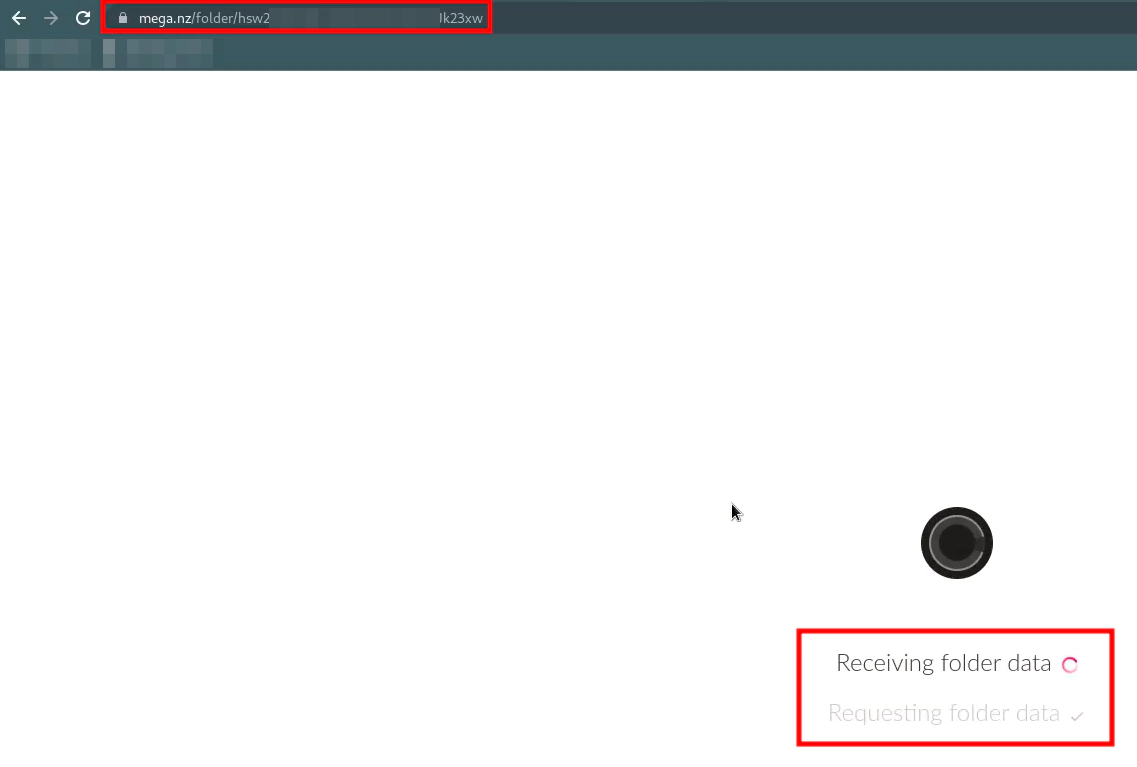
Open any MEGA public link with Data (more than 20GB) in the browser in which your MEGA account is signed in.
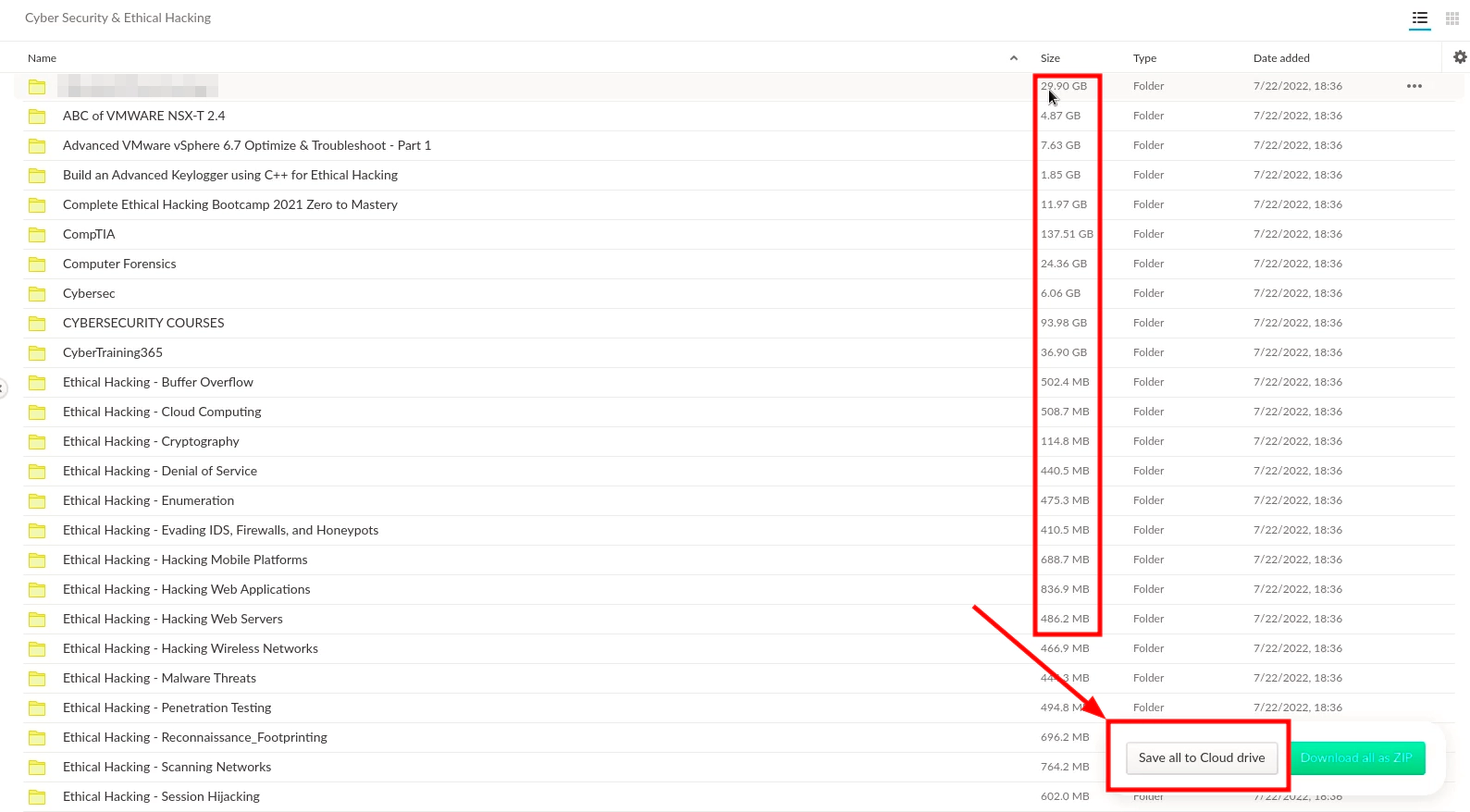
Try importing data into your account, which has a storage limit of 20GB.
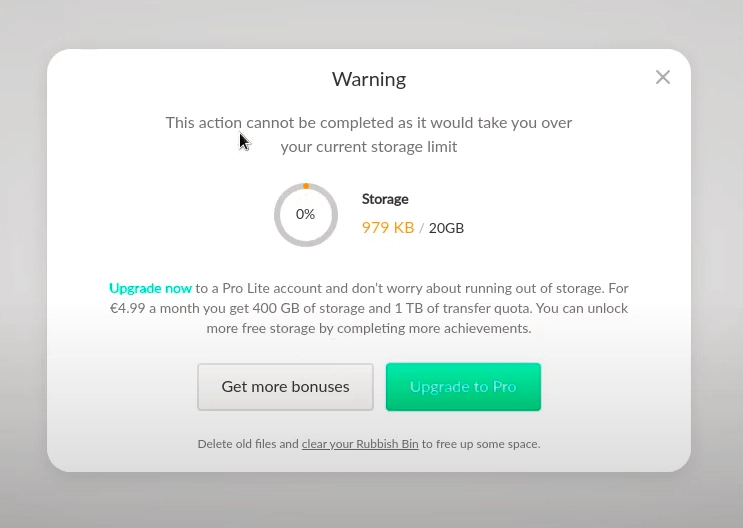
As intended by the MEGA developers, the Web Version will not allow you to IMPORT more than your storage capacity.
Now, open the same URL on the MEGA Mobile App.
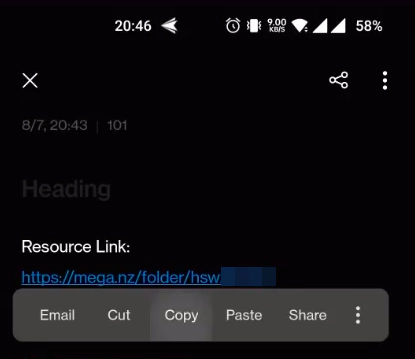
By clicking the IMPORT button on the app, you can try to IMPORT data into your account.
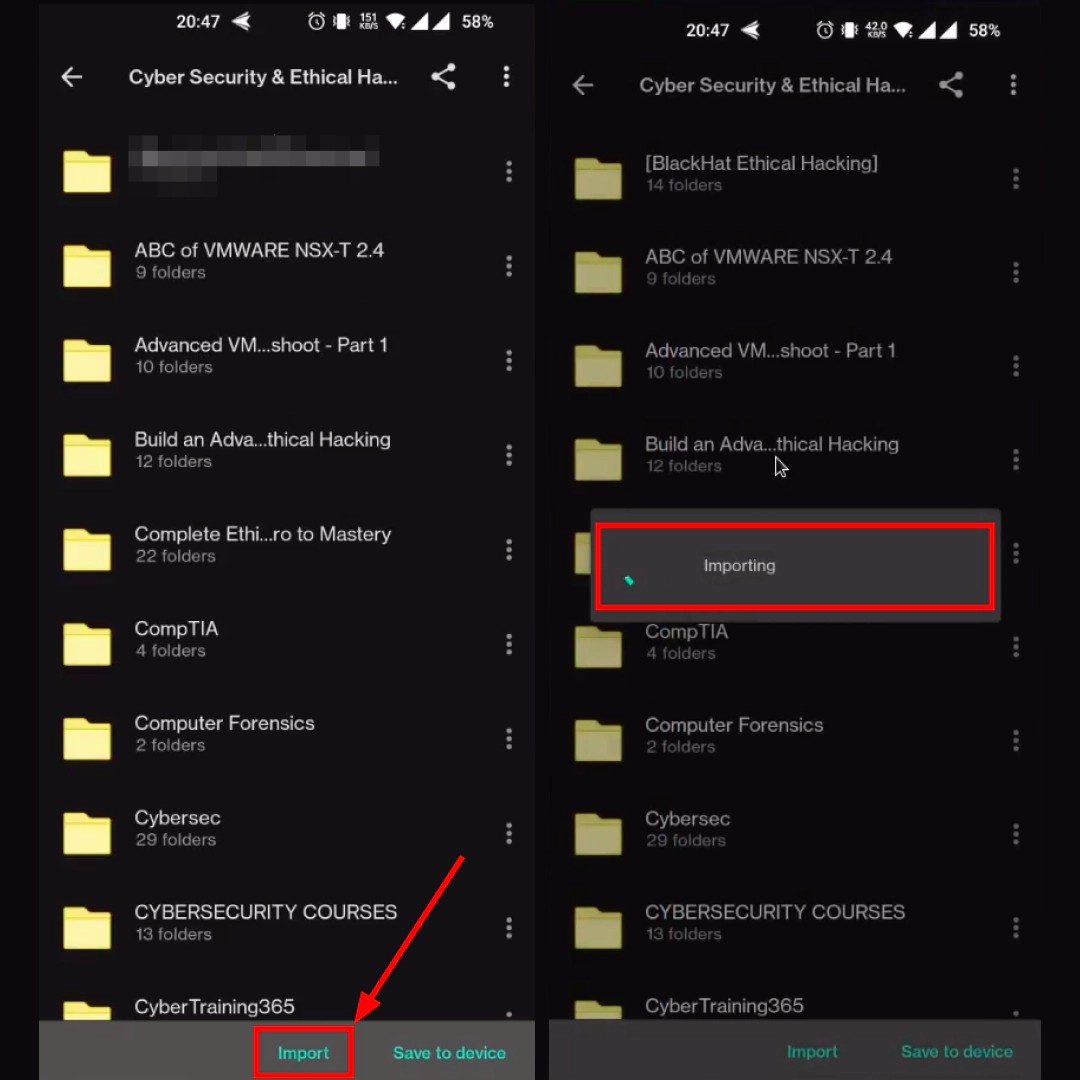
Navigate to your Mega account and you will find that all material from the MEGA URL has been copied to your MEGA Account despite the Storage Limitation.
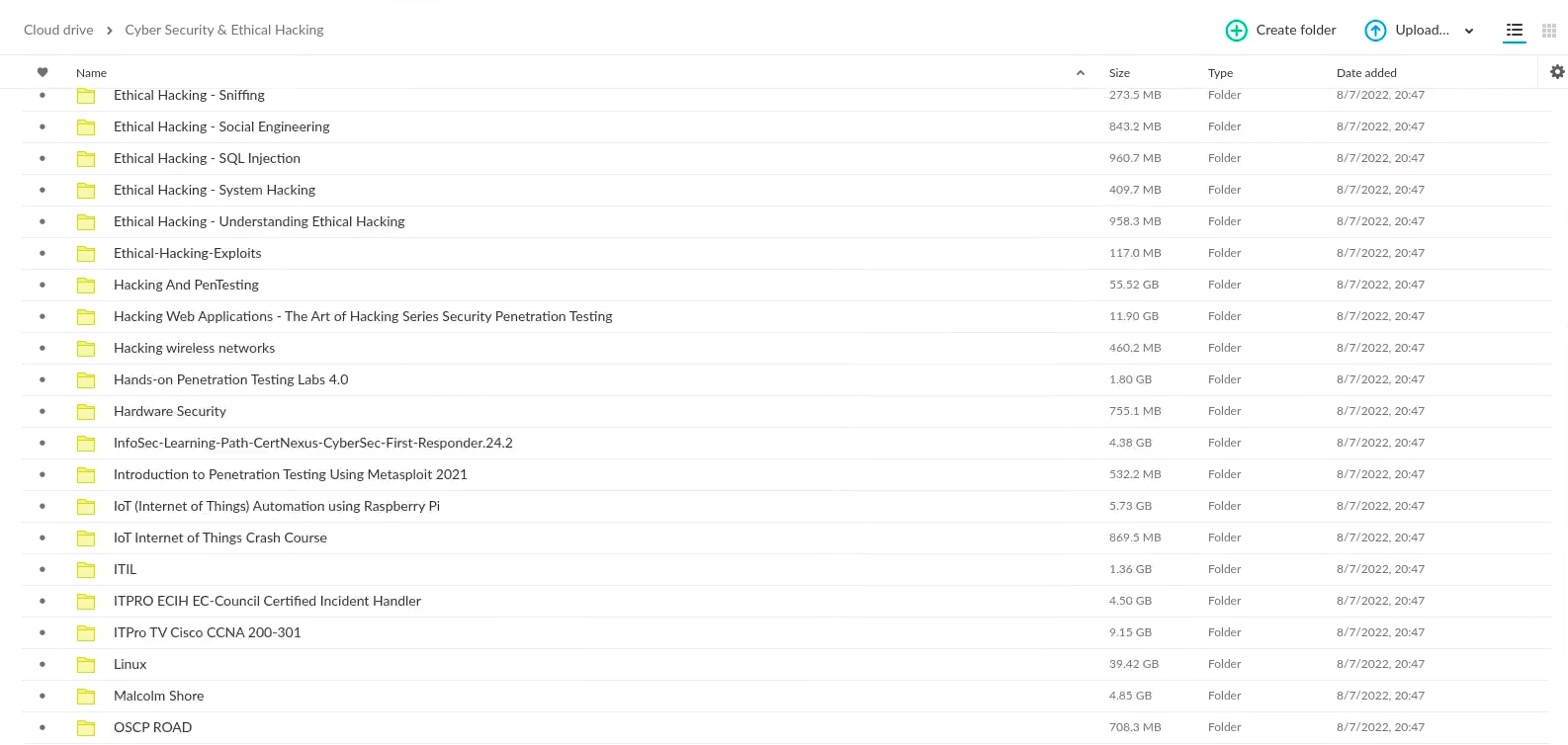
What could be the cause of this?
As previously stated, I did not use any tools and did not intercept the request, so I am unsure, but I believe it was due to MEGA’s APIs. MEGA, in my opinion, has separate APIs for mobile apps and web applications, and it seems that the mobile application API was failing to validate subscription plan, resulting in the vulnerability being spotted through mobile application.
Disclosure
The MEGA team has now fixed the vulnerability, and I am disclosing it to all with the permission of a MEGA Engineer and Co-Founder, Mr. Mathias Ortmann.